I am an Associate Professor and leader of the MINDS Lab group in the Software and Computer Systems division at the KTH Royal Institute of Technology, Sweden.
My research spans computer networking and AI-driven software systems, with a particular focus on Internet architectures, AI data centers, protocol design, and the intersection of security, privacy, and automation. Recently, I have been exploring AI-based code generation and verification as a foundation for building more reliable, secure, and explainable systems, combining formal methods with machine learning to advance intelligent infrastructure, and applications to networking.
Prior to join KTH, I was a postdoctoral researcher in the INL networking group at the Université catholique de Louvain and a postdoctoral researcher at the Hebrew University of Jerusalem. In 2013, I was a visiting scholar in the Berkeley NetSys Lab at the University of Berkeley I received my Ph.D. from Roma Tre University in 2014, advised by Prof. Giuseppe Di Battista.
News
New funded project. Our project on Democratizing Trustworthy Software Development will receive a generous 8.7MSEK of funding from Digital Futures. Our goal is to combine formal verification and AI-driven code generation for making software development reliable without requiring programming expertise. This is a collaboration with Martin Monperrus (KTH) and Mariano Scazzariello (RISE).
Paper accepted. Our work on transferring KV caches among LLM models had been accepted at ICLR 2026. Congratulations to Xiangyu Shi on his first accepted paper just a few months after starting his doctoral studies!
New funded project. Together with CanaryBit, Ericsson, Nvidia, Red Hat, RISE, and SAAB, we will work on a 27MSEK (2.5M EUR) project focusing on securing AI-based cloud-edge infrastructures.
New funded project. We have received funding from Digital Futures to work on a demonstrator project for resilient edge robotics.
New industrial doctoral student with Nvidia. We look forward to pushing the boundaries of today’s high-speed networking systems in modern datacenters. Welcome, Alexandra! Link to the collaboration announcement.
Paper accepted. Our work, accepted at Usenix NSDI 2026, reveals that where you store a packet matters. We show that smart payload placement can drastically cut energy use in terabit-scale NF systems. By tapping into switch buffer queues, we build the first energy-efficient, high-speed packet pipeline—delivering per-flow processing at terabit-per-second rates using just one commodity server and an ASIC switch.
Paper accepted. A joint work with RedHat and Emil Stahl, a master student at KTH, has been accepted for publication at the ANRW workshop. Congratulations, Emil!
Funding granted. Our project on AI-based code verification had been granted funding from WASP. I am hiring two doctoral students to join this exciting adventure!
Paper accepted. Our preliminary work on scheduling LLM inferences on a GPU has been accepted at the EuroMLSys workshop.
Applied Networking Research Prize! Our work on large language models and network management has received the IRTF/IETF Applied Networking Research Prize. Congratulations to Changjie, the recipient of the award!
Three papers accepted at LLM4Code. Our work on 1) generating verifiable code, 2) discovering software vulnerabilities, and 3) reducing the size of code-generation transformer-based models have been accepted for publication at the LLM4Code workshop!
Runner-up best paper. Our work on benchmarking LLMs for network management tasks has been shortlisted for the best paper award at ACM CoNEXT 2024.
Paper accepted. Our work on accelerating network functions by storing payloads on a high-speed switch has been published at the EuroP4 2024 workshop.
Paper accepted. Our work on accelerating network functions with differnet levels of flow-level granularities has been accepted at ACM CoNEXT 2024.
Talk at Nvidia. I was thrilled to present our ongoing work within the SEMLA project, including results from our accepted CoNEXT'24 paper, within the research seminars organized by Nvidia.
Paper accepted. Our work on quantifying the benefits and challenges of using Large Language Models for configuring networks has been accepted at ACM CoNEXT 2024.
Talk at 5G Italy. It was my great pleasure to present our ongoing work on using LLMs for orchestrating networks at the 5G Italy event.
Welcome Mohammad! Mohammad Siavashi will start his doctoral studies in our group, focusing on systems for large language models.
Best paper at CoNEXT. Congratulations to Mariano and Tommaso for leading our work on supporting million of state insertions in ASIC switches, which has received the best paper award at CoNEXT.
Welcome Changjie! Changjie Wang will start his doctoral studies in our group from Dec. 1. Welcome on board!
Paper accepted. Congratulations to our visiting postdoc, Thiago, on his paper acceptance at NOMS 2024. Thiago and co-authors demonstrate the possibility of using GANs to train RL-based models while retaining simulation accuracy.
Talk at Global Connect. I will be giving a talk on our SEMLA project (i.e., LLMs for network management) at the workshop organized in Paris before CoNEXT. I look forward to interesting discussions.
Project funding. Our 12-million SEK project on harnessing large language models for cybersecurity has been granted by Vinnova. This is a collaboration with RedHat, RISE, and Saab.
Paper accepted at CoNEXT. Our work on supporting million of low-latency flow-state insertions in terabit-per-second ASIC switches has been accepted to ACM CoNEXT! Congrats to Mariano and Tommaso who led the work!.
Summer internship time. This year we have three students taking a summer internship in our group. Welcome to Chaitanya (working on FPGAs), Changjie (working on GPT), and Parnian (working on ML for health-care).
Talk at Politecnico di Milano. I had the great pleasure to share our recent NSDI work (Ribosome) within the group led by Gianni Antichi. It was incredibly rewarding to receive so many excellent questions!
Talk at Aalto University. I had the great pleasure to share our recent work towards accelerating network functions in a talk at Aalto University in Helsinki hosted by Mario Di Francesco.
Alexandros' talk at RIPE SEE. Alexandros presented our work on BGP stealthy attacks at RIPE SEE. A link to the video of the talk is available here.
Welcome Thiago! During the next six month, we will be hosting Thiago Caproni Tavares as a postdoctoral fellow. He will be working on ML for networking.
Talk at RedHat. It was great to have the opportunity to present in a keynote our three recent works on terabit-per-second network functions at the PerfConf organized by RedHat. Thanks Simone Ferlin for the kind invitation.
Paper accepted. The work led by Alexandros Milolidakis on analyzing the effectiveness of the BGP public monitoring infrastructure in detecting sophisticated BGP attacks has been accepted for publication in IEEE Access.
Paper accepted at SIGMETRICS! Our work on analyzing the impact of multi-pipe ASIC switch architectures on network monitoring applications has been accepted at ACM Sigmetrics 2023. The paper is available here.
IS1200: Computer Hardware Engineering! Starting from this year, I will inherit and teach a bachelor course on computer architectures. The course activities that have been organized over the years are spot on, with an incredible amount of opportunities to learn a variety of aspects about how processors operate + hands-on experience on real hardware devices with project activities.
End of the year summary. It has been a fantastic 2022! Research-wise, Hamid presented Reframer at NSDI 2022 and we got an accepted paper for NSDI 2023. We also received a conditional acceptance notification for a paper at SIGMETRICS 2023. We also filed four patent applications on high-speed network functions in collaboration with Ericsson. We received funding from Digital Futures to continue our Emergence project and we received an Intel gift for different programmable devices that we will deploy in our lab. I had the priviledge to give a keynote at ACM CoNEXT where I could talk about our last three years of research. Teaching-wise, we are now back on campus and we can finally meet students for real (as opposed to blank screens on Zoom)! It is such a pleasure to see the curiosity and energy from the students in a physical class. We look forward to an even better 2023 year!
Funded project. Emergence 2.0 on Securing Edge Networks with a Programmable Intelligent Architecture has been funded with a Research Pair Consolidator Grant by KTH Digital Futures!
Invited keynote at ACM CoNEXT 2022. I received a kind invitation to give a keynote at ACM CoNEXT. Thanks to Justine Sherry and Marinho Barcellos, the TPC co-chairs, for inviting me.
NSDI TPC invitation. I will serve as a TPC member for the upcoming Usenix NSDI 2024.
Camera-ready of Ribosome (NSDI 2023) available. In this work accepted at NSDI 2023, we leverage emerging network disaggregation paradigms to dramatically push the performance boundary of general-pupose CPU packet processors. We demonstrate almost 300 Gbps of throughput for a variety of memory-intensive per-flow stateful network functions including rate limiters and packet schedulers. The camera-ready of the paper is available here. Find all the code here.
Castor Days on SDN at KTH. We organized a full-day even on Software-Defined Networking at KTH within the Castor Software Research Center in collaboration with Ericsson and SAAb. We had top-notch talks from both academia and industry. A video is available here.
Paper accepted at NSDI. Our work on novel approaches for realizing terabits-per-second stateful network functions has been accepted to NSDI 2023.
Alexandros' licentiate defense. On June 14, Alexandros Milolidakis has successfully defended his licentiate thesis titled "Understanding the Capabilities of Route Collectors to Observe Stealthy Hijacks". I would like to thank the advanced reviewer Prof. Gerald Q. Maguire Jr., the special reviewer Prof. Alberto Dainotti, and the examiner Prof. Roberto Guanciale.
Community Award at USENIX NSDI 2022. We are honoured to receive the "Community Award" at the NSDI 2022 conference for the best paper whose code and/or data set is made publicly available by the final papers deadline. Award screenshot
Docentship!I have officially become a Docent in Algorithms for Computer Networks.
Talk at the MARSAL workshop. I presented our recent efforts towards multi-Tbps stateful P4 packet processing during the MARSAL workshop organized by NVidia and NEC. The recording link will come soon.
Talk at the Durham university. I presented an extended version of our NSDI'20 work on high-speed load balancers during the Nestid seminars at Durham university.
Distinguished TPC member at INFOCOM! "This distinction is awarded based upon ratings by peer TPC members, fairness in review scores, and promptness in meeting various deadlines during the review process." This is the third time in the last four years that I am honored to receive this recognition. Awarded to 100 out of 465 TPC reviewers.
Intel hardware grant! A huge thank to Intel for awarding our research with an Intel hardware grant. We can now expand our experiments on Tofino dapataplanes with embedded FPGAs.
Promotion! I have been promoted to Associate Professor! A huge and heartfelt thanks to all my collaborators and previous advisors as well as all the support from KTH, the EECS school, and the Computer Science department.
Patent filed. We filed a patent on "System and method for accurate traffic monitoring on multi-pipeline switches" in collaboration with Ericssson Research.
Talk at Digital Future. I gave a seminar on building high-speed datacenter load balancers at Digital Futures.
PC chair at SIGCOMM demos. I will serve as a co-chair at ACM SIGCOMM Posters and Demos 2022. This year demos are planned to be held on site! We look forward to receive your most exciting and creative demonstrations!
VR Starting Grant funded! My project proposal "ResoNet: Resilient Optimized Network Synthesis" has been funded by a VR Starting Grant with 4M SEK (400K EUR). The project will start in 2022.
VR project funded! Together with Dejan Kostic, Magnus Boman, and Sabine Koch, our project "Scalable Federated Learning" has been funded by a VR Project with 3.8 MSEK (380K EUR). The proejct will start in 2022.
Talk at Digitalize Stockholm. I gave a short talk about our ongoing research on high-speed machine learning for network cybersecurity at Digitalize Stockholm. You can find the short video here on Youtube.
TPC Invitation. I will serve as a TPC member for Euro P4 2021! We look forward to seeing your latest work on programmable dataplanes!
Paper accepted! Our extended version of the Cheetah LB from NSDI'20 has been accepted for publication in the IEEE/ACM Transactions on Networking journal. We are now also supporting uniform and resilient load balancing of QUIC traffic!
Paper accepted! Deliberately delaying packets may sound like a bad idea for latency-critical system. Yet, we show that when the delay is limited, this can bring dramatic packet processing performance gains (up to 80% of additional throughput in practice). Don't miss our upcoming talk at USENIX NSDI 2022.
Summer internships! Two master students will join our group during hte summer to work on ML-based traffic classification.
Paper accepted! Our work on designing a decentralized SDN-based Internet eXchange Point (IXP) network has been accepted for publication at the IEEE Transactions on Network Science and Engineering journal. The key idea is to distribute the SDN responsibilities among the IXP networks instead of centralizing them at a single entity.
WASP industrial grant funded! Together with Simone Ferlin (Ericsson), we received an "industrial doctoral student" grant to work on disaggregated datacenters.
Paper accepted! Our work on benchmarking different data structures for supporting connection tracking has been accepted at HPSR! This is the first work of Massimo, who started his doctoral studies in our groups just five months ago, which has been co-supervised with Tom Barbette.
Paper accepted (and master thesis defense)! Our preliminary work on predicting the load on Kubernetes clusters has been accepted at EuroMLSys! This work is the result of a fantastic effort from Thomas Wang during his master thesis under the supervision of Simone Ferlin at Ericsson. Come to see Thomas' talk on April 26!
Welcome Fabio! We are really happy to host Fabio Verdi, an associate professor at the Federal University of Sao Carlos, for one year here at KTH. He plans to make programmable networks as resilient and performant as possible.
TPC invitation! I will serve as a TPC member for TMA 2021! We look forward to seeing your latest work on Internet network measurements!
Survey paper accepted! Our survey on fast failover techniques has been accepted at IEEE Communications Surveys and Tutorials! We cover aspects of network robustness ranging from Ethernet, and IP networks, to BGP and the emerging SDN and P4 programmable networks. A technical report can be found here.
PC invitation! I will serve as a TPC member for ICNP 2021! Please consider submitting a paper on your latest work on Internet network protocols.
TPC co-chair invitation. I will serve as a TPC co-chair at ACM CoNEXT 2021. We are looking forward to building a strong and exciting technical program for the conference.
Demo co-chair invitation. I will serve as a co-chair at ACM SIGCOMM Demo 2021. This year demos will be held virtually. We look forward to receive your most exciting and creative demonstrations!
Paper accepted! Our measurement of high-speed multi-100G Network Interface Cards (NICs) has been accepted for publication at PAM'21.
Paper accepted! An extended version of our CoNEXT'19 work on fast reroute with programmable switches has been accepted for publication in IEEE/ACM Transactions on Networking.
PC invitation! I will serve as a TPC member for the PAM 2021 conference! Share your latest measurements with the community!
Poster accepted! Our preliminary work on intra-core data center load balancing has been accepted as a poster at ACM CoNEXT. See the extended abstract here.
PC invitation! I will serve as a TPC member for the CoNEXT Student workshop 2020! We are looking for students who wants to share their preliminary work with the broader networking research community!
PC invitation! I will serve as a TPC member for EuroP4 2020! We are looking forwards to seeing your latest work on top of programmable devices!
Welcome Giacomo and Massimo! We have two new PhD students joining our group at KTH, Giacomo Verardo and Massimo Girondi. Giacomo plans to overcome today's scalability limitations of federated learning approaches. Massimo plans to harness the new powerful functionalities of the emerging SmartNICs to enhance today's network services.
PC invitation! I will serve as a TPC member for INFOCOM 2021! We are looking forwards to seeing your latest work!
Summer internship! Erfan Wu will join us for a summer internship to work on advanced datacenter load balancing in QUIC.
The EMERGENCE project has been funded by the Digital Future intiative! Stay tuned for more updates!
Awarded the IEEE ComSoc William R. Bennett Prize! I am extremely honored to have received the IEEE Communication Society William R. Bennett Prize for our Transactions on Networking paper titled "Traffic Engineering with ECMP: An Algorithmic Perspective". The prize is awarded to the single best publication of an original paper published in the IEEE/ACM Transactions on Networking or the IEEE Transactions on Network and Service Management in the previous three calendar years.
PC invitation! I will serve as a TPC member for CoNEXT 2020! Please consider submitting a paper on your latest networking work.
2nd Distinguished TPC member at INFOCOM! "This distinction is awarded based upon ratings by peer TPC members, fairness in review scores, and promptness in meeting various deadlines during the review process." Awarded to 100 out of 433 TPC reviewers.
Paper accepted to ACM CCR! Our work "Path Persistence in the Cloud: An empirical study of the effectsof Traffic Engineering in the AWS Network" has been accepted to ACM CCR.
PC invitation! I will serve as a TPC member for ICNP 2020! Please consider submitting a paper on your latest work on Internet network protocols.
Paper accepted at NSDI! I am very happy to announce that "A High-Speed Load-Balancer Design with Guaranteed Per-Connection-Consistency" got accepted to NSDI. This paper was a collaboration within the NSLab at KTH and two internship students from our master program!
The SE-CAID Datalab will be funded by Vinnova! I am very excited to announce that we received funding for building the SE-CAID datalab, whose objective is "to deploy a national telecom and digitalization data lab that broadly supports industrial and academic R&D, allowing for industries, SMEs and academia to share a broad range of telecom data and AI models". Stay tuned for more updates!
Farhad successfully defended his master thesis! In his thesis, Farhad investigated the problem of modeling a function describing the link "criticality" for Traffic-Engineering purposes. Link to the thesis on DiVA KTH (not yet available).
Paper accepted at CCR! Our survey on Internet peering interconnection practices has been accepted to ACM CCR.
PURR received the "Artefact Evaluated - Reusable" ACM badge at CoNEXT'19! The badge represents the highest recognition for a work whose data and code has been made available to the public and the results of the paper easy to reproduce.
Featured at RIPE Labs, at APNIC blog, and video of the talk at RIPE'79! Our ongoing work on inter-datacenter load balancing has been summarized in a recent blog post at RIPE Labs and APNIC blog. I also presented our work at the RIPE79 meeting. A video of the talk is available here.
Henrik successfully defended his master thesis! In his thesis, Henrik investigated the feasibility of realizing highly resilient fast reroute mechanisms on highly programmable switches. Link to the thesis on DiVA KTH (not yet available).
Two papers accepted at CoNEXT'19! Both PURR, a general programmable primitive for fast failover and our study on leveraging database normalization theory to model programmable packet processing pipelines have been accepted to CoNEXT'19.
Finalist for the Facebook Networking Systems research award! I reached the finals for the Facebook Networking Systems research award thanks to our recent work on stateless load balancers.
Welcome Hamid! A new PhD student has joined our group at KTH, Hamid Ghasemirahni. He plans to boost the performance of today's wide-area communication on commodity devices.
Selected by the RIPE RACI for presenting our work at the RIPE'79 meeting! I will present our recent study on Cloud inter-datacenter performance at the upcoming 79'th RIPE meeting in Rotterdam! Many thanks to the RIPE RACI initiative for inviting us to present it.
Summer internships! Chen Tang and Haoran Yao joined us for a summer internship to work on advanced datacenter load balancing.
Invited talk! I gave a talk on Robust and Scalable Internet Routing
at the NSF workshop on "Foundations of Internet Routing" at Cornell University (New York, US). Thanks to Nate Foster, Dexter Kozen, Robert Kleinberg, and Praveen Kumar for the kind invitation and the great organization!
Invited talk! I gave an invited lecture on SDN and programmable networks
at the ITN school on "SDN and multi-tenancy in mobile networks" at Ericsson (Kista, Sweden). Thanks to Christos Verikoukis for the kind invitation and Peter Ohlen for hosting the event!
Dagstuhl workshop! I have attended a fantastic workshop on "Programmable dataplane networks" in Dagstuhl (Germany) perfectly organized by Gianni Antichi, Theophilus Benson, Nate Foster, Fernando Ramos, and Justine Sherry!
PC invitation! I will serve as a TPC member for INFOCOM 2020! Please consider submitting a paper on your latest networking work.
PC invitation! I will serve as a TPC member for ICNP 2019! Please consider submitting a paper on your latest work on Internet network protocols.
Distinguished TPC member at INFOCOM! "This distinction is awarded based upon ratings by peer TPC members, fairness in review scores, and promptness in meeting various deadlines during the review process." Awarded to 100 out of 464 TPC reviewers.
Teaching starts again! I am very excited to give for the first time the Advanced Internetworking II course at KTH. We are going to explore the Link Layer (Layer 2) and try to understand how it ended up incorporating many of the Network Layer (Layer 3) functionalities!
Welcome Alexandros! A new PhD student has joined the NSLab at KTH, Alexandros Milolidakis. He plans to discover novel ways to secure Internet routing from a variety of different attacks.
Raheem successfully defended his master thesis! In his thesis, Raheem studied novel SDN-based approaches to secure IXPs from so-called unwanted traffic attacks. Link to the thesis on DiVA KTH.
PC invitation! I will serve as a TPC member for HPSR 2019! We are looking forward to seeing your latest work on switching and routing!
PC invitation! I will serve as a TPC member for the Asia-Pacific Workshop on Networking (APNet) 2019! We are looking forward to seeing your newest work on computer networking and systems!
Student Research Competition final at SIGCOMM! Together with Professor Zhi-Li Zhang (University of Minnesota), we organized the ACM Student Research Competition in parallel with the SIGCOMM conference. A video of the SRC award session can be found here.
PC invitation! I will serve as a TPC member for CCGrid 2019! Please consider submitting a paper on your latest cluster, cloud, and grid computing work.
Talk at P4 workshop! I presented our work on Fast Reroute in P4 at the P4 workshop in Stanford! PDF
Paper accepted! "Prelude: Ensuring Inter-Domain Loop-Freedom in SDN-Enabled Networks" has been accepted to the The Second Asia-Pacific Workshop on Networking (APNet'18)!
Two posters accepted! Our posters "Dynam-IX: a Dynamic Interconnection eXchange" and "Picking a Partner: A Fair Blockchain Based Scoring Protocol for Autonomous Systems" have been accepted to the Applied Networking Research Workshop (ANRW 2018)!
Paper accepted! "Supporting Emerging Applications With Low-Latency Failover in P4" has been accepted to the ACM SIGCOMM 2018 Workshop on Networking for Emerging Applications and Technologies (NEAT 2018)!
Talk at RIPE'76! I presented our Dynam-IX project at the 76th RIPE meeting in Marseille! Many thanks to the RIPE RACI initiative for inviting us to present our most recent work: video.
PC invitation! I will serve as a TPC member for the ACM CoNEXT Student Workshop 2018! Please consider submitting a paper on your latest networking work.
Paper accepted! "Oblivious Routing in IP Networks" has been accepted to Transactions on Networking!
PC invitation! I will serve as a TPC member for INFOCOM 2019! Please consider submitting a paper on your latest networking work.
Paper accepted! "Moving Bits with a Fleet of Shared Virtual Routers" has been accepted to IFIP Networking 2018!
PC invitation! I will serve as a TPC member for ICNP 2018! Please consider submitting a paper on your latest work on Internet network protocols.
Paper accepted! "TI-MFA: Keep Calm and Reroute Segments Fast" has been accepted to GI 2018!
Moved to KTH as an Assistant Professor!
PC invitation! I will serve as a TPC member for LANMAN 2018! We are looking forward to seeing your latest work on networking!
PC invitation! I will serve as a TPC member for the Poster and Demo session at SOSR 2018! We are looking forward to seeing your current work on networking!
Paper presentation! I presented SIXPACK at CoNEXT'17!
PC invitation! I will serve as a TPC member for HPSR 2018! We are looking forward to seeing your latest work on switching and routing!
Co-chair invitation! I will co-chair the SIGCOMM Student Research Competition 2018! More information to come!
PC invitation! I will serve as a TPC member for the APNeT 2018! We are looking forward to seeing your newest work on computer networking and systems!
PC invitation! I will serve as a TPC member for the EuroSys Doctoral Workshop 2018! Please consider submitting your current work and present it at a prestigious venue!
PC invitation! I will serve as a TPC member for SOSR 2018! Please consider submitting a paper on your latest work on Software Defined Networking!
Paper accepted! SIXPACK has been accepted to CONEXT 2017!
Paper accepted! "ENDEAVOUR: A Scalable SDN Architecture for Real-World IXPs" has been accepted to JSAC 2017!
PC invitation! I will serve as a TPC member for CCGrid 2018! Please consider submitting a paper on your latest cluster, cloud, and grid computing work.
Poster accepted! "Privacy-Preserving Detection of Inter-Domain SDN Rules Overlaps" has been accepted to SIGCOMM 2017!
PC invitation! I will serve as a TPC member for INFOCOM 2018! Please consider submitting a paper on your latest networking work.
Demo accepted! "SDN-enabled Traffic Engineering and Advanced Blackholing at IXPs" has been accepted to SOSR 2017!
PC invitation! I will serve as a TPC member for ICNP 2017! Please consider submitting a paper on your latest work on Internet network protocols.
Paper accepted! "Decentralized Consistent Updates in SDN" has been accepted to SOSR 2017!
Paper accepted! "PrIXP: Preserving the Privacy of Routing Policies at Internet eXchange Points" has been accepted to IM 2017!
PC invitation! I will serve as a TPC member for SWFAN 2017 (Infocom workshop)! Please consider submitting a paper on your latest Software-Driven Flexible and Agile Networking work.
PC invitation! I will serve as a TPC member for ITC 2017! Please consider submitting a paper for Area 2: Future Internet Architectures (incl. SDN, NFV, HPC, ICN, CCN).
Paper accepted! On the Resiliency of Static Forwarding Tables has been accepted to Transaction on Networking!
Paper accepted! COYOTE has been accepted to CONEXT 2016!
Paper accepted! Traffic Engineering with ECMP has been accepted to Transaction on Networking!
Paper accepted! SIXPACK has been accepted to the Applied Networking Research Workshop in Berlin!
Paper accepted! ez-Segway has been accepted to the Applied Networking Research Workshop in Berlin!
Paper accepted! On the Resiliency of Randomized Routing Against Multiple Edge Failures has been accepted to ICALP!
Paper presentation! I presented "The Quest for Static Resilient Routing Tables" at INFOCOM 2016!
Key themes: Code verification, Code generation, AI, LLM, Software Engineering
In our project, called TRUST-SW, we will research about approaches to verify AI-generated code with no or minimal human supervision. We focus on accurately translating natural language intents into formal verification specifications, generating correct proofs, and testing models in real-world testbeds.
Start/end date: 2026 - 2029
Budget: 8.7 MSEK (total); 2.7 MSEK for our group
Funding body: Digital futures

Key themes: Code verification, Code generation, AI, LLM, Software Engineering
The Prometheus project addresses the growing risks of software failures that can disrupt critical systems and services. Its goal is to improve software reliability by ensuring programs are mathematically correct. To overcome the traditional complexity of this process, Prometheus integrates artificial intelligence to make verification faster and more accessible.
Link to demo: Video
Start/end date: 2025 - 2030
Budget: 2x doctoral students
Funding body: Wallenberg AI, Autonomous Systems and Software Program (WASP)

Key themes: Cyber-security, cloud-edge infrastructures
SAFIR is a collaborative project between academia (KTH, RISE) and industry (CanaryBit, Ericsson, Nvidia, RedHat, Saab) aiming to build secure, resilient, and trustworthy cloud-edge infrastructures. It focuses on two main goals: (1) enabling trusted execution of AI workloads across cloud and edge environments, and (2) developing secure AI-driven control mechanisms for automated cloud orchestration.
Partners: CanaryBit, Ericsson, Nvidia, Red Hat, RISE, SAAB
Start/end date: 2025 - 2028
Budget: 27M SEK (2.5M EUR) total; 7M SEK at KTH
Funding body: The Swedish Innovation agency (Vinnova)

Key themes: Edge-cloud continuum, vision language models
EdgeWise is a research initiative developing the next generation of trustworthy humanoid robots. The project focuses on improving responsiveness, reliability, and safety through innovative computing and verification techniques that enable robots to operate effectively even under challenging connectivity conditions.
Start/end date: 2025 - 2027
Partners: RISE
Budget: 2MSEK (180k EUR) total; 600k SEK at KTH
Funding body: Digital Futures

Key themes: Network sythesis, benchmarking, machine learning, programmable networks, high-speed forwarding, SDN, P4, algebra
Internet networks are essential to our society. Yet, recent trends have shown a growing friction between the assumptions made decades ago and the unprecedented scale at which today's networks operate. Global electricity consumption of datacenter networks are expected to rise from 1% to 20% by 2030. To reduce energy usage, operators must today accurately capture low-level details of all the devices in a network and their traffic characteristics. As an example, the throughput of a network card may drop by 90% depending on the incoming traffic.
In this proposal, called ResoNet, we propose an ambitious research agenda that aims at developing new network synthesis methods that guarantee performance and robustness requirements. Based on our preliminary results, this may reduce energy usage of the datacenter servers by a factor of 3x.
Start/end date: 01 Jan 2022 - 31 Dec 2026
Budget: 4M SEK (400K EUR)
Funding body: Vetenskaprådet (VR) Starting Grant

Key themes: Large Language Models, cyber-security, resilience, software development, computer networks
The SEMLA project seeks to make the development of software systems more resilient, secure, and cost-effective. SEMLA leverages recent advancements in machine learning (ML) and artificial intelligence (AI) to automate critical yet common & time-consuming tasks in software development that often lead to catastrophic security vulnerabilities. SEMLA aims to achieve the following three objectives: (i) quickly learning about new vulnerabilities, (ii) enabling developers to generate secure code, (iii) realizing resilient infrastructure.
Link: project blog.
Start/end date: 01 Nov 2023 - 31 Oct 2025
Project cost: 12M SEK (1M EUR)
Funding body: Vinnova

Key themes: Machine learning, programmable networks, high-speed forwarding, SDN, P4
Thwarting cyberattacks is a complex problem. Traditional network technologies are not designed to learn how to distinguish legitimate traffic from malicious one but rather to forward traffic towards their destinations at the highest possible speed. In this project, called EMERGENCE, we will overcome the aforementioned challenges by designing, implementing, and deploying the first ML framework tailored for high-speed real-time network cybersecurity applications. The project is highly interdisciplinary, requiring in-depth knowledge from the fields of machine learning and network systems. To analyze the inherent volatile nature of Internet traffic, EMERGENCE will study novel scientific approaches to extract information from high-speed network devices at increasing levels of granularity.
Start/end date: 01 Jan 2021 - 31 Dec 2024
Budget: 4M SEK (400K EUR)
Other partners: RISE
Funding body: KTH Digital Futures

Key themes: Machine learning, data lab, telecommunication digital data
The objective of SE-CAID is to deploy a national telecom and digitalization data lab that broadly supports industrial and academic R&D, allowing for industries, SMEs and academia to share a broad range of telecom data and AI models. SE-CAID will be focused on: 1) building a platform and API that allows for open and controlled access of data (in distributed and centralised way) and 2) developing a process to handle the legal aspects of sharing data that does not fall into the category of open data sets.
Start/end date: 06 Dec 2019 - 05 Dec 2021
Budget: 4.5M SEK (450K EUR)
Other partners: RISE, Lund University, Ericsson, STOKAB
Funding body: Vinnova

Key themes: Programmable switches, layer-4 load balancing, P4, SDN, QUIC, TCP
Large service providers use load balancers to dispatch millions of incoming connections per second towards thousands of servers. There are two basic yet critical requirements for a load balancer: uniform load distribution of the incoming connections across the servers and per-connection-consistency (PCC), i.e., the ability to map packets belonging to the same connection to the same server even in the presence of changes in the number of active servers and load balancers. Yet, meeting both these requirements at the same time has been an elusive goal. Today’s load balancers minimize PCC violations at the price of non-uniform load distribution.
Our objective is to build highly efficient load balancer mechanisms that enable arbitrary server selection mechanisms and guarantee PCC. Check our ongoing efforts below.
View on GitHub » Read about our Cheetah LB » Watch the Cheetah talk »

Key themes: Internet Exchange Point, SDN, BGP, Network Management
The focus of the project is to enable added-value services to be provided thanks to Software-Defined Networking (SDN), on top of Internet Exchange Points and other network interconnnection fabrics. The services would relate not only to the flexibility of the interconnection fabric, but most importantly to enable the content and data center ecosystem that is present at the interconnection fabric to collaborate. The ultimate goal is to create a service marketplace on top of the ecosystem composed of Cloud/data centers, networked applications, and the interconnection fabric.
The objective of ENDEAVOUR is to address current limitations of the Internet interconnection model, as well as to open the opportunity for novel services, creating the possibility for new economic models around the created ecosystems.
Website: www.h2020-endeavour.eu
Start/end date: 01/01/2015 - 31/12/2017
Budget: 4.2M EUR
Other partners: Queen Mary University of London, University of Cambridge, DE-CIX, LAAS-CNRS, IBM Zurich
Funding body: EU Horizon 2020

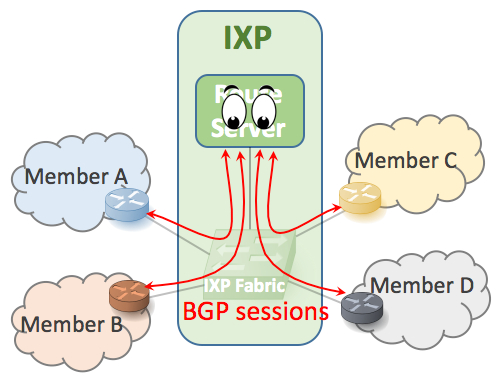
Key themes: Internet Exchange Point, BGP, privacy preservation
Internet eXchange Points (IXPs), where a quickly increasing number of networks exchange routing information, play an ever growing role in Internet inter-connection. To facilitate the exchange of routes among their members, IXPs provide Route Server (RS) services to dispatch the routes according to each member's peering policies. Nowadays, to make use of RSes, these policies must be disclosed to the IXP. This poses fundamental questions regarding the privacy guarantees of route-computation on confidential business information. Indeed, as evidenced from interaction with IXP administrators, and survey of network operators, this state of affairs raises privacy concerns among network administrators and even deters some networks from subscribing to RS services. We design an RS service that leverages Secure Multi-Party Computation (SMPC) techniques to keep peering policies confidential, while maintaining, and even extending, the functionalities of today's RSes. We assess the effectiveness and scalability of our system by evaluating a prototype implementation using traces of data from one of the largest IXPs in the world. Our evaluation results indicate that our RS system can scale to support privacy-preserving route-computation even at IXPs with many hundreds of member networks.
View on BitBucket » Read our short paper » Watch our talk »
Join work with : Marco Canini (KAUST), Daniel Demmler (TU Darmstadt), Michael Schapira (HUJI), Thomas Schneider, (TU Darmstadt)
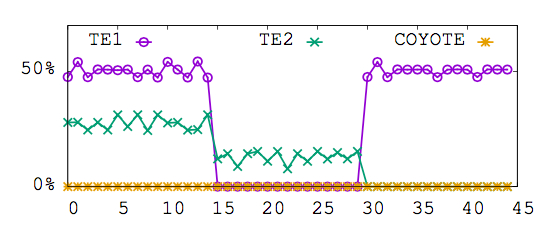
Key themes: Traffic Engineering, SDN, traffic uncertainty
To optimize the flow of traffic in IP networks, operators do traffic engineering (TE), i.e., tune routing-protocol parameters in response to traffic demands. TE in IP networks typically involves configuring static link weights and splitting traffic between the resulting shortest-paths via the Equal-Cost-MultiPath (ECMP) mechanism. Unfortunately, ECMP is a notoriously cumbersome and indirect means for optimizing traffic flow, often leading to poor network performance. Also, obtaining accurate knowledge of traffic demands as the input to TE is elusive, and traffic conditions can be highly variable, further complicating TE. We leverage recently proposed schemes for increasing ECMP's expressiveness via carefully disseminated bogus information ("lies") to design COYOTE, a readily deployable TE scheme for robust and efficient network utilization. COYOTE leverages new algorithmic ideas to configure (static) traffic splitting ratios that are optimized with respect to all (even adversarially chosen) traffic scenarios within the operator's "uncertainty bounds". Our experimental analyses show that COYOTE significantly outperforms today's prevalent TE schemes in a manner that is robust to traffic uncertainty and variation. We discuss experiments with a prototype implementation of COYOTE.
Joint work with: Gábor Rétvári (Budapest University of Technology and Economics), Michael Schapira (HUJI)
Key themes: SDN, robustness, resiliency, fast failover
Fast Reroute (FRR) and other forms of immediate failover have long been used to recover from certain classes of failures without invoking the network control plane. While the set of such techniques is growing, the level of resiliency to failures that this approach can provide is not adequately understood. In this paper, we embarked upon a systematic algorithmic study of the resiliency of forwarding tables in a variety of models (i.e., deterministic/probabilistic routing, with packet-header-rewriting, with packet-duplication). Our results show that the resiliency of a routing scheme depends on the ``connectivity'' $k$ of a network, i.e., the minimum number of link deletions that partition a network. We complement our theoretical result with extensive simulations. We show that resiliency to $4$ simultaneous link failures, with limited path stretch, can be achieved without any packet modification/duplication or randomization. Furthermore, our routing schemes provide resiliency against $k-1$ failures, with limited path stretch, by storing $\log(k)$ bits in the packet header, with limited packet duplication, or with randomized forwarding technique.
Joint work with: Andrei Gurtov (Linkoping), Aleksander Madry (MIT), Slobodan Mitrovic (EPFL), Ilya Nikolaevskiy (Aalto), Aurojit Panda (UC Berkeley), Michael Schapira (HUJI), Scott Shenker (ICSI/UC Berkeley)

Key themes: Traffic Engineering, ECMP, computational complexity
To efficiently exploit network resources operators do traffic engineering (TE), i.e., adapt the routing of traffic to the prevailing demands. TE in large IP networks typically relies on configuring static link weights and splitting traffic between the resulting shortest-paths via the Equal-Cost-MultiPath (ECMP) mechanism. Yet, despite its vast popularity, crucial operational aspects of TE via ECMP are still little-understood from an algorithmic viewpoint. We embark upon a systematic algorithmic study of TE with ECMP. We first consider the standard “splittable-flow” model of TE with ECMP, put forth in [18]. We settle a long-standing open question by proving that, in general, even approximating the optimal link-weight configuration for ECMP within any constant ratio is an intractable feat. We also initiate the analytical study of TE with ECMP on specific network topologies and, in particular, datacenter networks. We prove that while TE with ECMP remains suboptimal and computationallyhard for hypercube networks, ECMP can, in contrast, provably achieve optimal traffic flow for the important category of folded Clos networks. We next investigate the approximability of TE with ECMP in the more realistic “unsplittable-flow” model and present upper and lower bounds for scheduling “elephant” flows on top of ECMP (as in, e.g., Hedera [4]). Our results complement and shed new light on past experimental and empirical studies of the performance of TE with ECMP.
Joint work with: Guy Kindler (HUJI), Michael Schapira (HUJI)
-
KVComm: Enabling Efficient LLM Communication through Selective KV Sharing
In International Conference on Learning Representations (ICLR), 2026
X. Shi, M. Chiesa, G. Q. Maguire Jr, D. Kostic,
[ Coming soon][
Coming soon][ arXiv]
arXiv]
-
Queue-Mem: Energy-Efficient Hardware Storage for Advanced Network Function Acceleration
In USENIX Symposium on Networked Systems Design and Implementation (NSDI), 2026
M. Scazzariello, T. Caiazzi, H. Ghasemirahni, D. Kostic, M. Chiesa
[ PDF]
PDF]
-
RAG Against the Machine: Zero-Shot Software Vulnerabilities
Classification using LLMs
In the International Workshop on Large Language Models for Code (LLM4Code), published within ICSE, 2026.
E. Nordqvist , C. Wang, S. Ferlin, M. Scazzariello, M. Chiesa
[ Coming soon]
Coming soon]
-
Toward Automated, Contamination-free Dafny Benchmark Generation
In Dafny workshop (co-located with POPL), 2026
C. Wang, M. Scazzariello, D. Kostic, M. Chiesa
[ Coming soon]
Coming soon]
-
Dissect-and-Restore: AI-based Code Verification with Transient Refactoring
In arXiv, 2025
C. Wang, M. Scazzariello, A. Alshnakat, R. Guanciale, D. Kostic, M. Chiesa
[ PDF]
PDF]
-
Can LLMs Forecast Internet Traffic from Social Media?
In arXiv, 2025
J. Langlet, M. Scazzariello, F. Luciani, M. Burocchi, D. Kostić, M. Chiesa
[ PDF]
PDF]
-
On the Benefits of Predictable Traffic in Virtual Switches: A Case Study
In IETF Applied Networking Research Workshop (ANRW), 2025
E. Ståhl, S. Ferlin, E. Chaudron, M. Chiesa
[ Coming soon]
Coming soon]
-
Priority-Aware Preemptive Scheduling for Mixed-Priority Workloads in MoE Inference
In Workshop on Machine Learning and Systems (EuroMLSys), 2025
M. Siavashi, F. K. Dindarloo, D. Kostić, M. Chiesa
[ PDF]
PDF]
-
From Scientific Texts to Verifiable Code: Automating the Process with Transformers
In the International Workshop on Large Language Models for Code (LLM4Code), published within ICSE, 2025.
C. Wang, M. Scazzariello, M. Chiesa
[ PDF]
[
PDF]
[ Demo video]
Demo video]
-
Automating the Detection of Code Vulnerabilities by Analyzing GitHub Issues
In the International Workshop on Large Language Models for Code (LLM4Code), published within ICSE, 2025.
D. Cipollone, C. Wang, M. Scazzariello,, S. Ferlin, M. Izadi D. Kostić, M. Chiesa
[ PDF]
PDF]
-
Deriving Coding-Specific Sub-Models from LLMs using Resource-Efficient Pruning
In the International Workshop on Large Language Models for Code (LLM4Code), published within ICSE, 2025.
L. Puccioni, A. Farshin, M. Scazzariello, C. Wang, M. Chiesa, D. Kostić
[ PDF]
PDF]
-
Deliberately Congesting a Switch for Better Network Functions Performance
In P4 Workshop in Europe (EuroP4), published within ICNP, 2024.
M. Scazzariello, T. Caiazzi, M. Chiesa
[ PDF]
PDF]
-
Just-in-Time Packet State Prefetching
In arXIV, technical report, 2024
H. Ghasemirahni, A. Farshin, D. Kostic, M. Chiesa
[ PDF]
PDF]
-
FAJITA: Stateful Packet Processing at 100 Million pps
In ACM International Conference on emerging Networking EXperiments and Technologies (CoNEXT), 2024
H. Ghasemirahni, A. Farshin, M. Scazzariello, G. Q. Maguire Jr., D. Kostic, M. Chiesa
[ PDF]
[
PDF]
[ GitHub Code]
GitHub Code]
-
NetConfEval: Can LLMs Facilitate Network Configuration?
In ACM International Conference on emerging Networking EXperiments and Technologies (CoNEXT), 2024
C. Wang, M. Scazzariello, A. Farshin, S. Ferlin, D. Kostic, M. Chiesa
[ PDF]
[
PDF]
[ GitHub Code]
[
GitHub Code]
[ HuggingFace Dataset]
[
HuggingFace Dataset]
[ arXiv]
[
arXiv]
[ Applied Networking Research Prize]
[
Applied Networking Research Prize]
[ Runner-up best paper award]
[
Runner-up best paper award]
[ ACM highlight]
[
ACM highlight]
[ KTH News]
[
KTH News]
[ RedHat Magazine (page 30)]
RedHat Magazine (page 30)]
-
Deploying Stateful Network Functions Efficiently using Large Language Models
In Workshop on Machine Learning and Systems (EuroMLSys), 2024
H. Ghasemirahni, A. Farshin, M. Scazzariello, M. Chiesa, D. Kostic
[ PDF]
PDF]
-
Reducing the number of leads for ECG Imaging with Graph Neural Networks and meaningful latent space
In Proceedings of the Statistical Atlases and Computational Modeling of the Heart (STACOM), 2024
G. Verardo, D. F. Perez-Ramirez, S. Bruchfeld, M. Boman M. Chiesa, S. Koch, G. Q. Maguire Jr., D. Kostic
[ PDF]
PDF]
-
FMM-Head: Enhancing Autoencoder-based ECG anomaly detection with prior knowledge
In Proceedings of the International Conference on Pattern Recognition and Artificial Intelligence (ICPRAI), 2024
G. Verardo, M. Boman, S. Bruchfeld, M. Chiesa, S. Koch, G. Q. Maguire Jr., D. Kostic
[ PDF]
[
PDF]
[ arXiv]
arXiv]
-
TimeGAN as a Simulator for Reinforcement Learning Training in Programmable Data Planes.
In IEEE/IFIP Network Operations and Management Symposium (NOMS), 2024
T. C. Tavares, L. C. de Almeida, W. R. D. Silva, M. Chiesa, F. L. Verdi
[ PDF]
PDF]
-
Millions of Fast State Insertions on ASIC Switches
In ACM International Conference on emerging Networking EXperiments and Technologies (CoNEXT), 2023
T. Caiazzi, M. Scazzariello, M. Chiesa
[ PDF]
[
PDF]
[ Code]
[
Code]
[ KTH news]
[
KTH news]
[ Best paper award]
Best paper award]
-
On the Effectiveness of BGP Hijackers That Evade Public Route Collectors
In IEEE Access, 2023
A. Milolidakis, T. Buhler, M. Chiesa, L. Vanbever, S. Vissicchio
[ PDF]
PDF]
-
Network Monitoring on Multi-Pipe Switches
In ACM Special Interest Group for the Computer Systems Performance Evaluation (SIGMETRICS), 2023
M. Chiesa, F. Verdi
[ PDF]
[
PDF]
[ Code]
[
Code]
[ Video]
Video]
-
A High-Speed Stateful Packet Processing Approach for Tbps Programmable Switches
In USENIX Symposium on Networked Systems Design and Implementation (NSDI), 2023
M. Scazzariello, T. Caiazzi, H. Ghasemirahni, T. Barbette, D. Kostic, M. Chiesa
[ PDF]
[
PDF]
[ Video]
[
Video]
[ Code]
Code]
-
Oscilloscope: Detecting BGP Hijacks in the Data Plane
In arXIV, technical report, 2023
T. Buhler, A. Milolidakis, R. Jacob, M. Chiesa, S. Vissicchio, L. Vanbever
[ PDF]
PDF]
-
Fast Server Learning Rate Tuning for Coded Federated Dropout
In Workshop on Trustworthy Federated Learning in Conjunction with IJCAI 2022 (FL-IJCAI), 2022
G. Verardo, D. Barreira, M. Chiesa, D. Kostic, G. Q. Maguire Jr.
[ PDF]
PDF]
-
Packet Order Matters! Improving Application Performance by Deliberately Delaying Packets
In USENIX Symposium on Networked Systems Design and Implementation (NSDI), 2022
H. Ghasemirahni, T. Barbette, G. Katsikas, A. Farshin, M. Girondi, A. Roozbeh, M. Chiesa, G. Q. Maguire Jr., D. Kostić
[ PDF]
[
PDF]
[ Video]
[
Video]
[ Code]
[
Code]
[ NSDI Community Award]
NSDI Community Award]
-
Extended abstract: Heavy Hitter Detection on Multi-Pipeline Switches
In P4 Workshop in Europe (EuroP4), published within ANCS, 2021.
F. Verdi, M. Chiesa
[ PDF]
PDF]
- Cheetah: A High-Speed Programmable Load-Balancer Framework with Guaranteed Per-Connection-Consistency
In IEEE/ACM Transactions on Networking (ToN), 2021.
T. Barbette, E. Wu, D. Kostic, G. Q. Maguire Jr., P. Papadimitratos, M. Chiesa
[ PDF]
[
PDF]
[ Code]
[
Code]
[ Video from NSDI]
[Slides from NSDI]
Video from NSDI]
[Slides from NSDI]
-
DeSI: A Decentralized Software-Defined Network Architecture for Internet eXchange Points
In IEEE Transactions on Network Science and Engineering (TNSE), 2021.
H. Mostafaei, D. Kumar, G. Lospoto, M. Chiesa, G. Di Battista
[ PDF ]
PDF ]
-
High-Speed Connection Tracking in Modern Servers
In IEEE High Performance Switching and Routing (HPSR), 2021.
M. Girondi, M. Chiesa, T. Barbette
[ PDF ]
[
PDF ]
[ Code]
Code]
-
Predicting CPU Usage for Proactive Autoscaling
In Workshop on Machine Learning and Systems (EuroMLSys), 2021.
T. Wang, S. Ferlin, M. Chiesa
[ PDF ]
[
PDF ]
[ Video]
[
Video]
[ Code]
Code]
-
What you need to know about (Smart) Network Interface Cards
In Passive and Active Measurement conference (PAM), 2021.
G. Katsikas, T. Barbette, M. Chiesa, D. Kostic, G. Q. Maguire Jr
[ PDF]
[
PDF]
[ Video]
[
Video]
[ Slides]
[
Slides]
[ Code]
Code]
-
A Survey of Fast Recovery Mechanisms in the Packed Switched Networks
In IEEE Communications Surveys and Tutorials (COMST), 2021.
M. Chiesa, A. Kamisinski, J. Rak, G. Retvari, S. Schmid
[ PDF]
PDF] - Fast ReRoute on Programmable Switches
In IEEE/ACM Transactions on Networking (ToN), 2021.
M. Chiesa, R. Sedar, G. Antichi, M. Borokhovich, A. Kamisiński, G. Nikolaidis, S. Schmid
[ Accepted version]
[
Accepted version]
[ Code]
Code]
-
Extended abstract: Stateless CPU-aware Datacenter Load-Balancing
In ACM International Conference on emerging Networking EXperiments and Technologies (Conext Posters), 2020
T. Barbette, M. Chiesa, G. Q. Maguire Jr, D. Kostic.
[ PDF]
PDF]
-
A High-Speed Load-Balancer Design with Guaranteed Per-Connection-Consistency
In USENIX Symposium on Networked Systems Design and Implementation (NSDI), 2020
T. Barbette, C. Tang, H. Yao, D. Kostic, G. Q. Maguire Jr., P. Papadimitratos, M. Chiesa
[ PDF]
[
PDF]
[ Video]
[Slides]
[
Video]
[Slides]
[ Code]
[
Code]
[ Facebook Networking Systems research runner-up award]
Facebook Networking Systems research runner-up award]
-
A Survey on the Current Internet Interconnection Practices
In ACM SIGCOMM Computer Communication Review (CCR), 2020
P. Marcos, M. Chiesa, C. Dietzel, M. Canini, M. Barcellos.
[ PDF]
PDF]
-
Path persistence in the cloud: A study of the effects of inter-region traffic engineering in a large cloud provider's network
In ACM SIGCOMM Computer Communication Review (CCR), 2020
W. Reda, K. Bogdanov, A. Milolidakis, H. Ghasemirahni, M. Chiesa, G. Q. Maguire Jr., D. Kostic.
[ PDF]
[
PDF]
[ Talk at RIPE]
[
Talk at RIPE]
[ Code]
[
Code]
[ APNIC coverage]
APNIC coverage]
-
Normal Forms for Match-Action Programs
In ACM International Conference on emerging Networking EXperiments and Technologies (CoNEXT), 2019
F. Nemeth, M. Chiesa, G. Retvari
[ PDF]
PDF] -
PURR: A Primitive for Reconfigurable Fast Reroute
In ACM International Conference on emerging Networking EXperiments and Technologies (CoNEXT), 2019
M. Chiesa, R. Sedar, G. Antichi, M. Borokhovich, A. Kamisiński, G. Nikolaidis, S. Schmid
[ PDF]
[
PDF]
[ Code]
[Slides]
Code]
[Slides]
-
Dynam-IX: a Dynamic Interconnection eXchange
In ACM International Conference on emerging Networking EXperiments and Technologies (CoNEXT), 2018
P. Marcos, M. Chiesa, L. Muller, P. Kathiravelu, C. Dietzel, M. Canini, M. Barcellos
[ PDF]
[
PDF]
[ Short video]
[
Short video]
[ Talk at RIPE]
[
Talk at RIPE]
[ Code]
[
Code]
[ Website]
Website]
-
Prelude: Ensuring Inter-Domain Loop-Freedom in SDN-Enabled Networks
In Asia-Pacific Workshop on Networking (APNet), 2018
A. Dethise, M. Chiesa, M. Canini
[ PDF]
PDF]
-
Supporting Emerging Applications With Low-Latency Failover in P4
In ACM Workshop on Networking for Emerging Applications and Technologies (NEAT), 2018
R. Sedar, M. Borokhovich, M. Chiesa, G. Antichi, S. Schmid
[ PDF]
PDF]
-
Oblivious Routing in IP Networks
In IEEE/ACM Transactions on Networking (ToN), 2018
M. Chiesa, G. Retvari, M. Schapira
[ PDF]
[
PDF]
[ Code]
Code]
-
Moving Bits with a Fleet of Shared Virtual Routers
In IEEE/IFIP Networking 2018
P. Kathiravelu, M. Chiesa, P. Marcos, M. Canini, L. Veiga
[ PDF]
PDF] -
TI-MFA: Keep Calm and Reroute Segments Fast
In IEEE Global Internet Symposium (GI), 2018
K. Foerster, M. Parham, M. Chiesa, S. Schmid
[ PDF] [Slides]
PDF] [Slides] -
SIXPACK: Securing Internet eXchange Points Against Curious onlooKers
In ACM International Conference on emerging Networking EXperiments and Technologies (CoNEXT), 2017
M. Chiesa, D. Demmler, M. Canini, M. Schapira, T. Schneider
[ PDF] [
PDF] [ Slides PDF]
[
Slides PDF]
[ Code]
[
Code]
[ Website]
Website]
-
ENDEAVOUR: A Scalable SDN Architecture for Real-World IXPs
In IEEE Journal of Selected Areas in Communications (JSAC), Special issue on Emerging Technologies in Software-driven Communication, 2017
G. Antichi, I. Castro, M. Chiesa, E. Fernandes, R. Lapeyrade, D. Kopp, J. Han, M. Bruyere, C. Dietzel, M. Gusat, A. W. Moore, P. Owezarski, S. Uhlig, M. Canini
[ PDF]
[
PDF]
[ Code]
[
Code]
[ Website]
Website]
-
Extended abstract: Privacy-Preserving Detection of Inter-Domain SDN Rules Overlaps
In ACM SIGCOMM Posters and Demos, 2017
A. Dethise, M. Chiesa, M. Canini
[ Extended Abstract] [
Extended Abstract] [ Poster]
Poster] - Demo: SDN-enabled Traffic Engineering and Advanced Blackholing at IXPs
In ACM Symposium on SDN Research (SOSR) Posters and Demos, 2017
C. Dietzel, G. Antichi, I. Castro, E. Fernandes, M. Chiesa
[ Extended abstract] [
Extended abstract] [ Poster]
Poster] -
Decentralized Fast Consistent Updates
In ACM Symposium on SDN Research (SOSR), 2017
T. D. Nguyen, M. Chiesa, M. Canini
[ PDF]
[
PDF]
[ Technical Report]
[
Technical Report]
[ Code]
Code]
-
PrIXP: Preserving the Privacy of Routing Policies at Internet eXchange Points
In IFIP/IEEE International Symposium on Integrated Network Management (IM), 2017
M. Chiesa, R. di Lallo, G. Lospoto, H. Mostafaei, M. Rimondini, G. Di Battista
[ Pre-print]
Pre-print] -
On the Resiliency of Static Forwarding Tables
In IEEE/ACM Transactions on Networking (ToN), 2017
M. Chiesa, I. Nikolaevskiy, S. Mitrovic, A. Gurtov, A. Madry, M. Schapira, S. Shenker
[ Pre-print]
Pre-print] -
Traffic engineering with Equal-Cost-Multipath: An algorithmic perspective
In IEEE/ACM Transactions on Networking (ToN), 2017
M. Chiesa, G. Kindler, M. Schapira
[ Pre-print]
[
Pre-print]
[ Code]
[
Code]
[ IEEE William R. Bennett Prize]
IEEE William R. Bennett Prize]
-
Lying Your Way to Better Traffic Engineering
In ACM International Conference on emerging Networking EXperiments and Technologies (CoNEXT), 2016
M. Chiesa, G. Retvari, M. Schapira
[ PDF] [
PDF] [ Slides]
[
Slides]
[ Code]
Code]
-
Towards Decentralized Fast Consistent Updates
In IETF Applied Networking Research Workshop (ANRW), 2016
T. D. Nguyen, M. Chiesa, M. Canini
[ PDF]
[
PDF]
[ Slides]
Slides] -
Extended abstract: Towards Securing Internet eXchange Points Against Curious onlooKers
In IETF Applied Networking Research Workshop (ANRW) Posters, 2016
M. Chiesa, D. Demmler, M. Canini, M. Schapira, T. Schneider
[ PDF] [
PDF] [ Poster] [
Poster] [ Slides]
Slides]
-
Inter-domain Networking Innovation on Steroids: Empowering IXPs with SDN Capabilities
In IEEE Communications Magazine (COMMAG) special issue on SDN Use Cases for Service Provider Networks, 2016
M. Chiesa, C. Dietzel, G. Antichi, M. Bruyere, I. Castro, M. Gusat, T. King, A. W. Moore, T. D. Nguyen, P. Owezarski, S. Uhlig, M. Canini
[ PDF]
PDF] -
On the Resiliency of Randomized Routing Against Multiple Edge Failures
In International Colloquium on Automata, Languages, and Programming (ICALP), 2016
M. Chiesa, A. Gurtov, A. Madry, S. Mitrovic, I. Nikolaevskiy, M. Schapira, S. Shenker
[ PDF]
[
PDF]
[ Technical Report on ArXiv] [
Technical Report on ArXiv] [ Slides]
Slides] -
The Quest for Resilient (Static) Forwarding Tables
In IEEE International Conference on Computer Communications (INFOCOM), 2016
M. Chiesa, I. Nikolaevskiy, S. Mitrovic, A. Gurtov and A. Madry, A. Panda, M. Schapira, S. Shenker
[ Pre-print]
[
Pre-print]
[ Technical Report on ArXiv] [
Technical Report on ArXiv] [ Slides]
Slides] -
Computational Complexity of Traffic Hijacking under BGP and S-BGP
In Theoretical Computer Science (TCS), 2015
M. Chiesa, G. Di Battista, T. Erlebach, M. Patrignani
[ Technical report]
Technical report]
-
Analysis of Country-wide Internet Outages Caused by Censorship
In IEEE/ACM Transactions on Networking (ToN), 2014
A. Dainotti, C. Squarcella, E. Aben, K. C. Claffy, M. Chiesa, M. Russo, A. Pescape'
[ PDF]
PDF]
-
The Role of Routing Policies in the Internet: Stability, Security, and Load-Balancing
Doctoral Thesis, Universita' degli Studi di Roma ``Roma Tre'', Dottorato di Ricerca in Ingegneria, Sezione Informatica ed Automazione, XXVI Ciclo, 2014
M. Chiesa
[ Thesis (PDF)] [
Thesis (PDF)] [ Presentation (PDF)]
Presentation (PDF)] -
Intra-Domain Routing with Pathlets
In Computer Communications (COMCOM), 2014
M. Chiesa, G. Lospoto, M. Rimondini, G. Di Battista
[ Technical report]
Technical report]
-
Traffic engineering with Equal-Cost-Multipath: An algorithmic perspective
In IEEE International Conference on Computer Communications (INFOCOM), 2014
M. Chiesa, G. Kindler, M. Schapira
[ Full Paper] [
Full Paper] [ Presentation at INFOCOM'14 ]
Presentation at INFOCOM'14 ] -
On the Area Requirements of Euclidean Minimum Spanning Trees
In Computational Geometry: Theory and Applications (CGTA), 2014. Special Issue on Selected Papers from WADS '11.
P. Angelini, T. Bruckdorfer, M. Chiesa, F. Frati, M. Kaufmann, C. Squarcella -
Using Routers to Build Logic Circuits: How Powerful is BGP?
In IEEE International Conference on Network Protocols (ICNP), 2013
M. Chiesa, L. Cittadini, L. Vanbever, S. Vissicchio, G. Di Battista
[ Presentation at ICNP'13 ]
[
Presentation at ICNP'13 ]
[ Best Paper]
Best Paper]
-
Intra-Domain Pathlet Routing
In IEEE International Conference on Computer Communications and Networks (ICCCN), 2013
M. Chiesa, G. Lospoto, M. Rimondini, G. Di Battista
[ Technical report]
[
Technical report]
[ Presentation at ICCCN'13]
Presentation at ICCCN'13] -
Computational Complexity of Traffic Hijacking under BGP and S-BGP
In International Colloquium on Automata, Languages and Programming (ICALP), 2012
M. Chiesa, G. Di Battista, T. Erlebach, M. Patrignani
[ Technical report] [
Technical report] [ Presentation at ICALP'12]
Presentation at ICALP'12] -
Analysis of Country-wide Internet Outages Caused by Censorship
In ACM Internet Measurement Conference (IMC), 2011
A. Dainotti, C. Squarcella, E. Aben, K. C. Claffy, M. Chiesa, M. Russo, A. Pescape'
[ PDF]
[
PDF]
[ IETF/ANRP prize]
IETF/ANRP prize]
-
On the Area Requirements of Euclidean Minimum Spanning Trees
In Algorithms and Data Structures Symposium (WADS), 2011
P. Angelini, T. Bruckdorfer, M. Chiesa, F. Frati, M. Kaufmann, C. Squarcella -
Local Transit Policies and the Complexity of BGP Stability Testing
In IEEE International Conference on Computer Communications (INFOCOM), 2011
M. Chiesa, L. Cittadini, G. Di Battista, S. Vissicchio
[ PDF]
[
PDF]
[ Presentation at INFOCOM'11]
Presentation at INFOCOM'11]
The Machine-Intelligence for Networks and Distributed Systems (MINDS) research group develops cutting-edge network systems with a focus on high performance, resilience, and sustainability. By uniquely integrating hardware and software programming, algorithmic theory, and artificial intelligence for system development, we aim to build the infrastructure and logic necessary for deploying next-generation applications.
Follow recent news from our group at our blog.
Team Members
Collaborations (a.k.a., co-supervision)
Current visitors
Alumni
Active master students
NonePast master students
Dániel Laki (with RISE), 2025
Thesis title: Exploring opportunities for code verification with Dafny using Large Language Models.
Edvin Nordqvist (with RedHat), 2025
Thesis title: Retrieval-Augmented Generation for Vulnerability Classification.
Kaiwen Ren (with RedHat), 2025
Thesis title: Credibility Assessment of Fabricated Bug Reports via Large Language Models.
Joar Gunnarsson (with Saab), 2025
Thesis title: Enhancing LLM Code Generation: Leveraging Expert Debugging Sessions and Fine-tuning for Better Code Generation.
Erik Halme (with Saab), 2025
Thesis title: Automating Data Plane Configuration: Leveraging LLMs for P4 Code Generation.
Zicheng Dong, 2025
-Thesis title: Architectural Characterization of In-Network Key-Value Stores: A Performance Evaluation on the NVIDIA BlueField-3 DPU.
Emil Ståhl (with RedHat), 2024
Thesis title: "Improving Megaflow Cache Performance in Open vSwitch with Coflow-Aware Branch Prediction". Link to PDF.
Laura Puccioni (with RISE), 2024
Thesis title: "Building Domain-Specific Sub-Models from Large Language Models using Pruning". Link to PDF.
Daniele Cipollone (with RISE), 2024
Thesis title: "Transformer-Based Models for Code Vulnerability Detection". Link to PDF.
Changjie Wang (with École Polytechnique), 2023
Thesis title: "Network Management Automation with LLMs".
Chenming Du, 2023
Thesis title: "Improving and Evaluating TRex Traffic Generator through P4 Switches". Link to PDF.
Jingyi Pan, 2023
Thesis title: "Improving network performance with a polarization-aware routing approach". Link to PDF.
Kunyu Wang, 2022
Thesis title: "Investigating the Effectiveness of Stealthy Hijacks against Public Route Collectors". Link to PDF.
Felix Maurer (with Ericsson), 2021
Thesis title: "Investigating Causes of Jitter in Container Networking". Link to PDF.
Zhe Wang, 2021
Thesis title: "Design and evaluation of an inter-core QUIC connection migration approach for intra-server load balancing". Link to PDF.
Mandar Joshi (with SAAB), 2021
Thesis title: "Implementation and Evaluation of In-Band Network Telemetry in P4". Link to PDF.
Haoran Yao, 2020
Thesis title: "The Design and Evaluation of a Seamless Approach to Migrate the State of QUIC Connections for Load Balancing Purposes". Link to PDF.
Thomas Wang (with Ericsson), 2020
Thesis title: "Predictive CPU autoscaling in containerized using Holt-winters exponential smoothing and LSTM networks".
Henrik Biorseth, 2019
Thesis title: "On the Feasibility of Deploying Highly Resilient Data Plane Forwarding Mechanisms Using Programmable Switches".
Farhad Zareafifi (with Ericsson), 2019
Thesis title: "Link Criticality Characterization for Network Optimization".
Muhammadd Raheem, 2018
Thesis title: "Mitigation of inter-domain Policy Violations at Internet eXchange Points". Link to PDF.
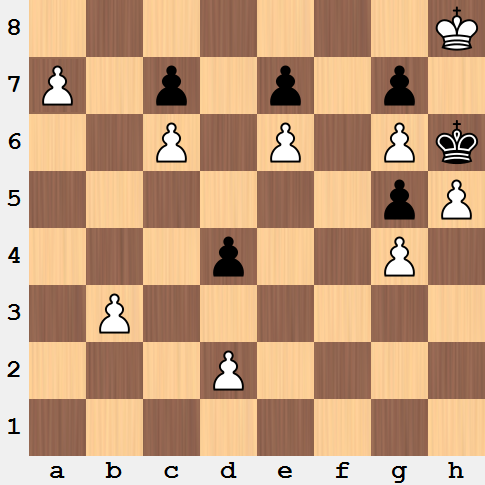
White to move. What is the best continuation to this brilliant chess puzzle?
You are forced to enter into a dark room. Inside the room, there is a table with $100$ non-overlapping coins placed on its surface. Each coin is either colored white or black. Once you enter the room, you cannot distinguish whether a coin has its upper side colored in black or white. You will be saved only if you will be able to partition the coins into two groups, each group with the same number of coins with the white side oriented upwards. You are allowed to flip the coins as many time as you want. Luckily, before entering the room, you overheard a vital information: 70 coins have their black side oriented upwards while the 30 remaining coins have their white side oriented upwards. Will you be able to survive?

There are $n$ prisoners serving a long-time sentence. One day, the director of the prison communicates them that the day after they will be disposed in a row in such a way that each prisoner will only be able to see the prisoners in front of him. Each prisoner will be wearing a hat, without knowing it color, which can be either black or white. As such, each prisoner does not know the color of its hat but he can see the color of the hats of the prisoners in front of him. Starting from the latter prisoner (the one that sees all the other prisoners), each prisoner will be asked to loudly guess the color of its hat by saying either "white" or black". Everyone can hear the answers. The prisoner will be killed if it fails to guess the color of its hat and it will be saved otherwise. The prisoners decides to agree on the strategy that guarantees the maximum number of survivors. How many people will survive for certain the day after?

Presentations at International Conferences
Videos
Links
Research
- Partial list of my publications on the DBLP Server
- Full list of my publications on my institutional web page
- ORCID: 0000-0002-5412-8136
- Scopus Author ID: 54793354100
- Google scholar: OXKn_G8AAAAJ
- Research Gate: Vincenzo_Roselli
Institutional web pages
- My personal home page at Roma Tre University
- My personal home page on the PhD School website
 kth.se
kth.se